Your data is your most valuable asset. We can help you to protect it.
Our Data Privacy and Protection knowledge and tools will help you to safeguard your business.
Your data is your most valuable asset. We can help you to protect it.
Our Data Privacy and Protection knowledge and tools will help you to safeguard your business.

Warrior Networks offers customers an array of managed security services designed to mitigate the risk of cyber-attacks. These services are built and operated within the UK, ensuring that data is kept onshore and secure. With a team of experienced specialists at the helm, we are able to quickly identify and focus on the most critical threats to our customers, providing real-time alerts and incident reports.
Our managed security services offer 24/7 coverage, alleviating the burden of constant monitoring for potential threats. Our expert security analysts work tirelessly to assure customer confidentiality, integrity, and availability. To maintain the highest levels of security, we adhere to best practice guidelines as set forth by industry regulatory bodies. Customers can rest assured that their data is in good hands with Warrior Networks.
Our managed security services encompass a wide range of security solutions, including threat detection, incident response, and vulnerability management. By continuously monitoring your IT environment, we ensure that any suspicious activity is promptly identified and addressed. This proactive approach helps to prevent potential breaches and minimize the impact of any security incidents.
At Warrior Networks, we understand that every business has unique security needs. That’s why our managed security services are tailored to meet the specific requirements of each customer. Whether you are a small business or a large enterprise, our scalable solutions are designed to grow with your business, providing the flexibility you need to stay ahead of evolving cyber threats.
Our team of security experts brings a wealth of experience and knowledge to our managed security services. We stay up-to-date with the latest developments in cybersecurity, ensuring that your IT infrastructure benefits from the most advanced protection available. Our commitment to continuous improvement means that we are always ready to address new challenges and opportunities in the ever-changing threat landscape.
One of the key benefits of our managed security services is the peace of mind it provides. Knowing that your IT security is managed by a team of professionals allows you to focus on your core business activities. Our 24/7 monitoring and support ensure that you always have the protection you need, regardless of the time of day or night.
In addition to threat detection and response, our managed security services also include comprehensive reporting and analysis. We provide detailed incident reports and regular updates on the status of your IT security, keeping you informed of any issues or improvements. Our transparent approach ensures that you always know what's happening with your systems and can make informed decisions about your security strategy.
Compliance with industry regulations and standards is a critical aspect of our managed security services. Warrior Networks conducts regular security audits to ensure that your IT systems comply with all relevant standards, reducing the risk of costly fines and enhancing your reputation with clients and partners. Our adherence to best practice guidelines helps you navigate the complex landscape of regulatory requirements with confidence.
Our managed security services are designed to be cost-effective, providing you with high-quality security solutions at a competitive price. By outsourcing your IT security to Warrior Networks, you can reduce the need for in-house security staff and infrastructure, lowering your operating costs while still benefiting from top-tier protection.
Choose Warrior Networks for expert managed security services that keep your business secure and compliant. Our dedicated team of security professionals is committed to protecting your IT infrastructure from cyber threats, ensuring the confidentiality, integrity, and availability of your data. With Warrior Networks as your security partner, you can focus on what you do best, knowing that your business is in safe hands.
Our managed SOC and XDR services offer top-of-the-line military-grade cybersecurity built upon market-leading technology. With our advanced threat detection and response capabilities, we ensure the safety of all endpoints, cloud instances, and IoT devices. Our efficient deployment and detection processes guarantee speedy security for modern hybrid organizations and critical systems. Additionally, our teams and ITSM integration provide a comprehensive solution to meet all your cybersecurity needs.
Managed SIEM & MDR with 24 x7 Automated
response in Teams Automated Response via Teams Monthly External Vulnerability Scanning Information Assurance Policy Library Cyber Security Maturity Assessment Tool
Managed SIEM, SOC & MDR with 24 x7 Threat Hunter response Automated Response via Teams Monthly External Vulnerability Scanning Information Assurance Policy Library Cyber Security Maturity Assessment Tool Annual External Penetration Test & Cyber Risk Management Portal
Managed SIEM, SOC, MDR & XDR with 24 x7 Threat Hunter response Automated Response via Teams Continuous Threat Attacking (Vulnerability Management & Penetration Testing) Automated Compliance updates & reporting Information Assurance Policy Library Cyber Security Maturity Assessment Tool Annual External, Internal and Web App Penetration Test & Cyber Risk Management Portal
The Warrior Networks service was developed with an emphasis on rapid on-boarding, utilizing automation to reduce the need for extensive security personnel and tools. This allows customers to efficiently respond to security events using the most current threat intelligence available. The service is tailored to suit the needs of organizations that already possess a SOC or prefer to handle their own alerts and alarms.
By using the DevOps pipelines this allows our developers to work together on a shared repository of code and as changes are made, there are automated build processes for detecting code issues. The outcome is a faster development life cycle and a lower error rate.
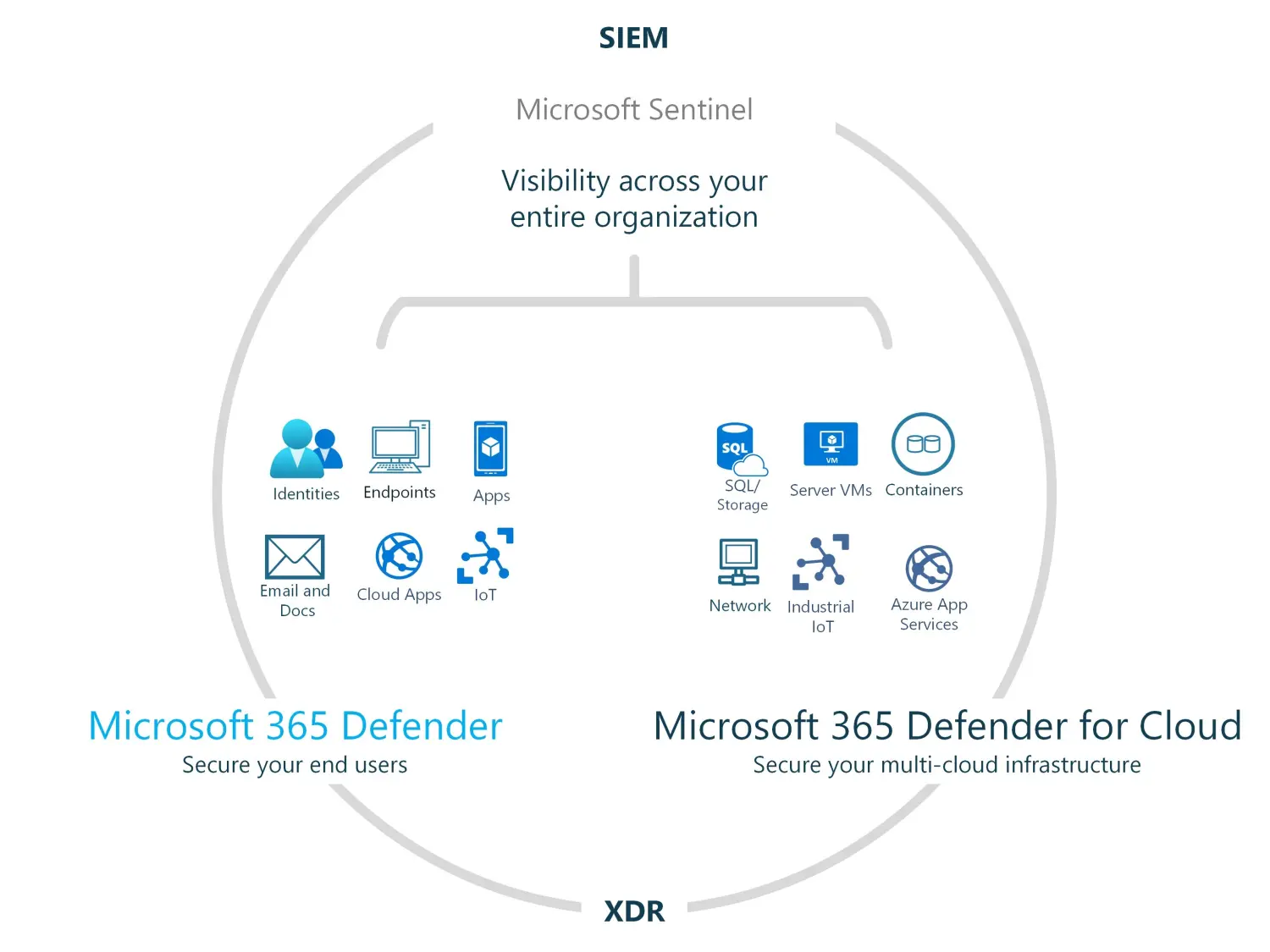
Microsoft 365 and Azure Security activity log data connectors are configured via our Sentinel-as-Code package for automated playbook responses. Automatic responses and collaboration via Microsoft Teams
Our enterprise security system is enhanced by a human touch, which serves to complement our automated processes. Our team of highly skilled Level 3 SOC Analysts carry out comprehensive threat searches, monitoring, reporting, containment and neutralization to ensure the safety of our enterprise.
By utilizing these threat indicators, it is possible to identify malicious activity that may be occurring within customer environments. This information can then be used to provide additional context to security investigators or playbooks, allowing for more informed response decisions to be made.
The dashboard for security incidents, specifically designed for analysts, is accessible along with supplementary online reports that record key performance indicators for managerial purposes.
The Log Analytics agent is employed to gather information from non-standard text file formats originating from both Windows and Linux systems. This information is then transferred to Microsoft Sentinel for analysis and parsing purposes.
By implementing CI/CD deployment, data connectors for various data sources can be seamlessly integrated into the customer's Microsoft Sentinel instance. This ensures that all relevant telemetry is ingested and available for analysis within Microsoft Sentinel.
The service is conducted quarterly, and it centers around agreed assets. Its main objective is to facilitate vulnerability scanning, scheduling, and support the customer in determining the appropriate course of action to respond to vulnerabilities that have been identified.
This service, which is conducted quarterly and only on mutually agreed upon assets, centers around scheduling and conducting vulnerability scans. Additionally, it offers assistance to the customer in determining an appropriate response plan for any vulnerabilities discovered.
Our subscription bundles for incident response offer unrestricted access to detect, isolate, and address any malevolent cyber incidents that may arise.
Standard log storage spans 1,000 days, providing a long-term solution for forensic investigations. This allows threat hunters to review historical security logs, ensuring data integrity, compliance, and easy retrieval. The logs are stored centrally to guarantee their integrity and ease of access.